AI Overview
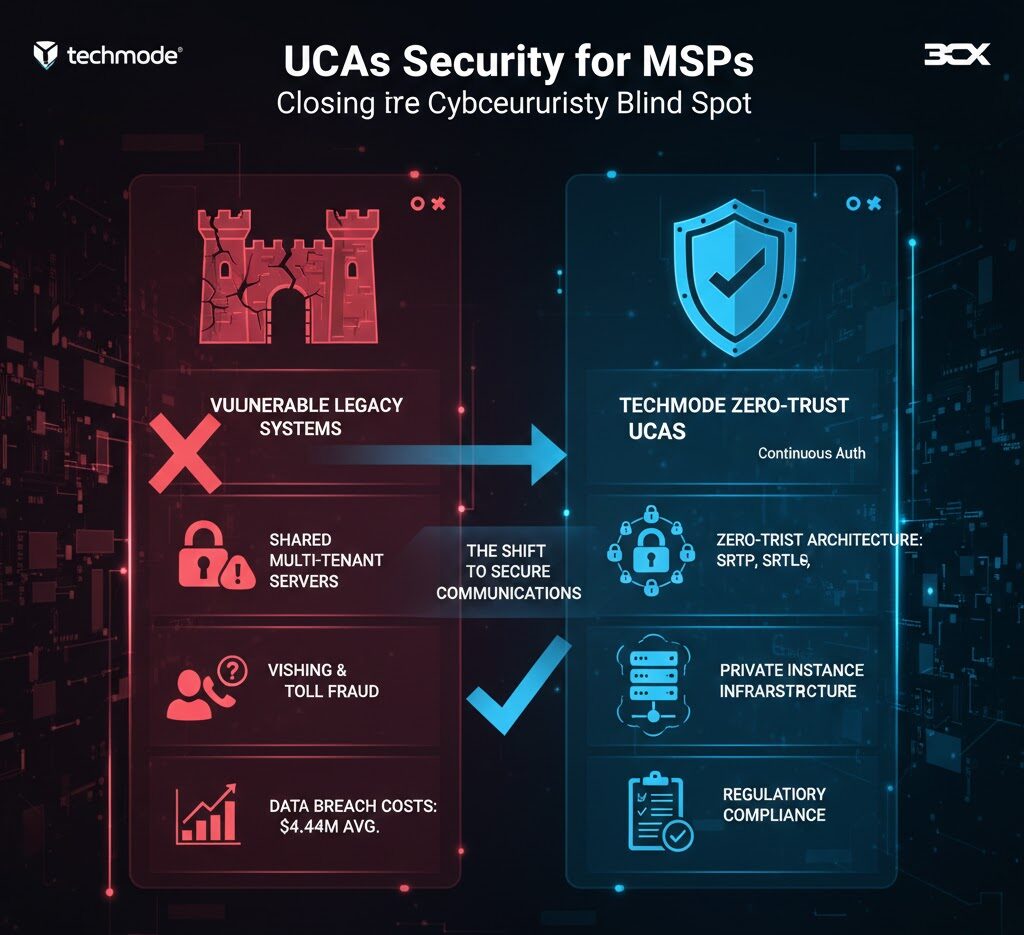
UCaaS security for MSPs is the cybersecurity blind spot most managed service providers don’t realize they have. While MSPs lock down endpoints, firewalls, and email, clients’ phone systems carry sensitive conversations, healthcare data, financial details, and compliance-regulated communications—often on shared multitenant servers with minimal security controls. Key UCaaS security priorities for MSPs in 2026 include: (1) zero-trust architecture requiring continuous authentication for every user and device, not just login-time MFA, (2) end-to-end encryption using AES-256, SRTP, and TLS to protect voice data in transit and at rest, (3) private instance infrastructure that isolates client data instead of sharing servers across tenants, and (4) regulatory compliance readiness, especially with the updated HIPAA Security Rule expected in May 2026 making encryption and MFA mandatory for all business associates. The average data breach costs $4.44 million (IBM, 2025), and MSPs who recommend insecure UCaaS platforms share that liability. Choosing a UCaaS partner with private AWS infrastructure, zero-trust capabilities, and built-in compliance eliminates security gaps without adding operational burden.
Somewhere in a server room right now, an MSP is meticulously configuring endpoint detection, deploying next-gen firewalls, and building zero-trust policies for every laptop, tablet, and IoT sensor in a client’s environment. Noble work.
Meanwhile, that same client’s phone system—the platform carrying sensitive customer conversations, financial details, and healthcare data—is sitting on a shared multitenant server with the security posture of an unlocked screen door. Nobody thought to ask.
UCaaS security for MSPs has become the cybersecurity blind spot that hackers are absolutely delighted about.
While managed service providers obsess over email filtering and ransomware prevention (rightfully so), the phone system quietly processes thousands of conversations per week with little scrutiny.
According to the World Economic Forum’s Global Cybersecurity Outlook 2025 report, 72% of cybersecurity leaders reported a rise in organizational risk over the past year.
VoIP and unified communications platforms aren’t exempt from that risk—they’re increasingly part of it.
This post breaks down why UCaaS security deserves the same attention MSPs give to every other piece of client infrastructure, what zero-trust architecture looks like when applied to business communications, and how encryption separates the secure platforms from the ones pretending to be.
The Phone System: The Last Unguarded Door in the Building
Most businesses treat their phone system like furniture. It exists, it works (mostly), and nobody thinks about it until something breaks.
MSPs inherit that mentality when they onboard clients, focusing security assessments on networks, endpoints, and cloud applications while the communication platform gets a pass.
That’s a problem, because modern UCaaS platforms carry everything: voice calls, video meetings, SMS/MMS messages, chat logs, voicemail transcripts, call recordings, and CRM-integrated data.
For healthcare clients, that includes protected health information (PHI). For financial services clients, that includes account details and compliance-sensitive conversations. For legal clients, that includes attorney-client privileged communications.
The average cost of a data breach hit $4.44 million in 2025, according to IBM’s annual Cost of a Data Breach report. Breaches involving data stored across multiple environments—like a UCaaS platform pulling data from cloud storage, CRM systems, and local devices—cost even more. IBM found that nearly 40% of data breaches affected multiple storage environments, with public cloud breaches averaging $5.17 million.
An MSP that locks down every endpoint but ignores the communication platform is essentially installing a state-of-the-art alarm system while leaving the back door wide open. And hackers don’t need an engraved invitation—they’ll find that door.
VoIP-Specific Threats MSPs Can’t Afford to Ignore
UCaaS security for MSPs isn’t just about generic cybersecurity best practices applied to a different platform.
VoIP and unified communications introduce attack vectors that don’t exist in traditional IT environments.
Here are the ones keeping security professionals up at night:
DDoS Attacks on SIP Infrastructure
Distributed denial-of-service attacks targeting VoIP systems flood Session Initiation Protocol (SIP) servers with incomplete call-signaling messages, consuming bandwidth until the system crawls to a halt or dies entirely.
An estimated 16 DDoS attacks occur every minute globally, and VoIP infrastructure is increasingly in the crosshairs. DDoS attacks in Q2 2025 were 44% higher than the same period in 2024. That’s not a trend line anyone should feel comfortable ignoring.
Vishing (Voice Phishing)
Vishing combines caller ID spoofing with social engineering to trick employees into revealing passwords, account numbers, or security codes over the phone. Social engineering became the top method for initial cyberattacks in 2025, accounting for 36% of all incidents, with phishing making up 65% of those cases. The voice channel is a goldmine for these attacks because most organizations train employees to spot suspicious emails but spend zero time on suspicious phone calls.
Eavesdropping and Call Interception
Without proper encryption, VoIP calls can be intercepted the same way unencrypted web traffic can. On public Wi-Fi—which remote employees use constantly—unencrypted voice packets are essentially broadcasting in the clear. Any halfway competent attacker with a packet sniffer can capture entire conversations.
Toll Fraud and System Hijacking
Attackers who gain access to a poorly secured VoIP system can rack up thousands of dollars in long-distance charges, use the system to launch spam campaigns, or leverage it as a launchpad for further network penetration. Open TCP and UDP ports on VoIP systems are common entry points.
MSPs who aren’t auditing their clients’ UCaaS security posture are leaving a massive gap in their managed services offering—one that clients will eventually notice, usually at the worst possible time.
Zero-Trust Architecture: Because “Trust But Verify” Was Always a Terrible Security Policy
The traditional “castle-and-moat” security model assumed everything inside the firewall was trustworthy. That assumption was dubious in 2010 and downright laughable in 2026.
With remote workers, BYOD policies, and cloud-based communication platforms, the castle walls crumbled years ago. Zero-trust architecture operates on a fundamentally different principle: never trust, always verify.
Applied to UCaaS, zero-trust means every user, every device, and every session must prove its legitimacy continuously—not just at login. As Telecom Metric’s analysis of Zero Trust Telephony explains, the voice perimeter is dead, and identity now replaces the firewall. Here’s what that looks like in practice:
Continuous Authentication
Multi-factor authentication (MFA) at login is table stakes. True zero-trust UCaaS goes further with continuous verification—monitoring behavior patterns, device context, login locations, and session anomalies in real time.
A login from Michigan at 9 AM followed by a login from Latvia at 9:15 AM should trigger immediate lockdown, not a polite email notification three days later.
Least Privilege Access
Not every employee needs access to call recordings, admin panels, or system configurations. Zero-trust UCaaS enforces role-based access controls (RBAC), granting users only the permissions necessary for their specific function. The receptionist doesn’t need the same system access as the IT administrator. (Though some receptionists could probably run the entire company—that’s a different conversation.)
Micro-Segmentation
Communication traffic gets segmented so that a breach in one area doesn’t cascade across the entire platform. If an attacker compromises a single user’s credentials, micro-segmentation contains the damage rather than handing them the keys to the kingdom.
Device Posture Verification
Before any device connects to the UCaaS platform, zero-trust models validate its security posture—checking patch levels, antivirus status, and OS compliance. That employee’s ancient laptop running Windows 8 and three expired antivirus trials? Denied at the gate.
By 2026, an estimated 80% of UCaaS platforms will incorporate some form of zero-trust architecture, including biometric authentication and end-to-end media protection.
MSPs who aren’t evaluating their UCaaS partners on zero-trust capabilities are falling behind the security curve.
Encryption: The Difference Between Secure and “We Wrote ‘Secure’ on the Website”
Encryption is the backbone of any legitimate UCaaS security strategy, but not all encryption implementations are created equal. Some providers encrypt data in transit. Some encrypt data at rest. The good ones do both.
The best ones implement end-to-end encryption so that not even the provider can access the content.
AES-256 Encryption
The industry gold standard for securing voice, video, and messaging data.
AES-256 (Advanced Encryption Standard with 256-bit keys) is resistant to brute-force attacks and widely regarded as the benchmark for protecting sensitive communications.
SRTP (Secure Real-Time Transport Protocol)
SRTP encrypts voice data packets during transmission, scrambling them into unreadable formats that can’t be deciphered even if intercepted.
Without SRTP, VoIP calls are essentially postcards—anyone who intercepts them can read the contents.
TLS (Transport Layer Security)
TLS protects signaling data like phone numbers, caller names, and session details. Combined with SRTP, it creates a comprehensive encryption layer that covers both the conversation content and the metadata surrounding it.
Here’s where it gets important for MSPs: the architecture of the UCaaS platform matters enormously. Multitenant platforms—where dozens or hundreds of customers share the same server infrastructure—create inherent security risks.
One tenant’s vulnerability becomes everyone’s vulnerability. Private instance deployments, where each client operates on dedicated infrastructure, eliminate that shared-risk exposure.
MSPs advising clients in regulated industries like healthcare, finance, or legal services should be asking their UCaaS provider exactly three questions:
What encryption standards do they implement?
Is client data isolated on private infrastructure?
And can they provide documentation proving compliance with HIPAA, GDPR, CCPA, or whatever regulatory framework applies?
If the answer to any of those questions involves the words “we’re working on it,” that’s the UCaaS equivalent of finding out the building’s fire extinguisher is actually a picture of a fire extinguisher.
Why MSPs Should Care About UCaaS Security (Beyond the Obvious)
Beyond the moral imperative of protecting client data, there’s a straightforward business case. Cyberattacks targeting software supply chains are expected to cost the global economy $80.6 billion annually by 2026. MSPs sit squarely in that supply chain. When a client’s communication platform gets compromised, the MSP that recommended and manages it shares the liability—reputational and potentially legal.
The upcoming HIPAA Security Rule update, expected to be finalized in May 2026, eliminates the old “addressable vs. required” flexibility that let organizations treat certain safeguards as optional.
Nearly all implementation specifications will become mandatory, including encryption of electronic protected health information (ePHI) in transit and at rest, multi-factor authentication for all system access, and 24-hour breach reporting requirements for business associates.
MSPs serving healthcare clients who recommend UCaaS platforms without enterprise-grade security are setting themselves up for compliance failures.
Additionally, 46% of all small and medium-sized businesses experienced a cyberattack in 2025, but only 14% said they were adequately prepared to defend against them.
That gap between threat exposure and preparedness is exactly where MSPs add value—and UCaaS security is an increasingly critical part of that value proposition.
How Techmode Handles UCaaS Security (So MSPs Don’t Have To)
All those threats, compliance requirements, and encryption standards can feel overwhelming—especially for MSPs who got into managed services to handle IT, not become telecom security specialists.
That’s precisely where the right UCaaS partner changes the equation.
Every TechmodeGO deployment runs on private, triple-redundant AWS instances—not shared multitenant platforms where one client’s security incident becomes everyone’s Tuesday morning crisis. Private infrastructure means isolated environments, dedicated resources, and security controls that don’t depend on the weakest tenant in the building keeping their passwords updated.
Techmode’s white-glove installation process includes security configuration from day one. Dedicated project managers and experienced install teams handle encryption setup, access controls, and compliance requirements before a single call goes live.
STIR/SHAKEN attestation, E911 compliance, and number registration? All managed automatically through Techmode’s infrastructure, eliminating the certification headaches MSPs dread.
After deployment, Techmode’s U.S.-based concierge support team—real technicians who answer in seconds, not offshore ticket queues—provides 24/7 assistance for both MSPs and their end clients.
With 99.999% uptime backed by private AWS infrastructure, an NPS of 85 (compared to the industry average hovering around 36), and an A+ BBB rating, Techmode delivers the security, reliability, and compliance that MSPs need without adding operational burden.
When MSPs partner with Techmode, UCaaS security stops being a liability and starts being a differentiator. That’s how managed service providers move from replaceable vendor to indispensable partner.
Ready to stop worrying about your clients’ phone system security? Explore the TechmodeGO Partner Program and see how channel-first UCaaS works in practice.
FAQs
Q: What is zero-trust architecture in UCaaS, and why does it matter for MSPs?
Zero-trust architecture operates on the principle of “never trust, always verify,” requiring continuous authentication and authorization for every user and device accessing the communication platform. For MSPs, this matters because clients’ remote workers, BYOD devices, and cloud-based communication tools have eliminated the traditional network perimeter. Zero-trust UCaaS ensures that compromised credentials or devices don’t cascade into full-scale breaches across client environments.
Q: How does UCaaS encryption protect against call interception?
UCaaS platforms use SRTP (Secure Real-Time Transport Protocol) to encrypt voice packets during transmission, making intercepted data unreadable. Combined with TLS for signaling data and AES-256 for data at rest, comprehensive encryption ensures that conversations, metadata, and stored recordings remain protected even if network traffic is compromised. Platforms without these encryption standards leave voice data exposed—essentially broadcasting conversations in plain text.
Q: Why is private instance UCaaS more secure than multitenant platforms?
Multitenant UCaaS platforms share server infrastructure among multiple customers, meaning one tenant’s security vulnerability can potentially expose others. Private instance deployments isolate each client on dedicated infrastructure, eliminating shared-risk exposure and providing independent security controls. For clients in regulated industries like healthcare or finance, private instances also simplify compliance by ensuring data isolation meets regulatory requirements.
Q: What UCaaS security questions should MSPs ask potential providers?
MSPs should ask about encryption standards (AES-256, SRTP, TLS), infrastructure architecture (private instance vs. multitenant), compliance certifications (HIPAA, GDPR, SOC 2), uptime guarantees with contractual SLAs, access control capabilities (MFA, RBAC), and breach notification procedures. Any provider that can’t answer these questions specifically—or deflects with marketing language—should raise immediate red flags.
Q: How does the 2026 HIPAA Security Rule update affect MSPs selling UCaaS to healthcare clients?
The updated HIPAA Security Rule, expected to be finalized in May 2026, makes nearly all security specifications mandatory rather than “addressable.” This includes required encryption of ePHI in transit and at rest, mandatory multi-factor authentication, annual compliance audits, and 24-hour breach reporting for business associates. MSPs recommending UCaaS platforms to healthcare clients need partners that meet these requirements natively—not platforms that require extensive customization to achieve basic compliance.